Information technology is a constantly changing industry, with practices shifting all the time. As a result, anyone you have working on your company’s IT should be actively seeking out various certifications to confirm that they are keeping up on modern trends and standards. To help you accomplish this, we’ve put together a brief list of valuable IT certifications that your IT personnel—whether they’re in-house employees or outsourced professionals—should have.
Apex Technology Blog
Each year, we take some time and take a look at the most interesting new smartphones that are being released. Over the past few years, fewer companies are making smartphones and throughout the whole industry, innovation has seemed to slow. Whether this is a result of rigid market dynamics, supply shortages, or the extraordinary costs it takes to manufacture and source components, it has taken some of the largest technology companies in the world—such as Amazon, LG, and HTC—out of the market and presented limited opportunities for other global technology leaders such as Microsoft, Sony, and Nokia.
In good times and bad, profitability is the priority for most businesses out there. Having said that, this priority is typically a challenging one to achieve, but did you know that there are a few different ways that investing in a relationship with a managed service provider can help increase your productivity—and as a result, your overall profitability?
AI—artificial intelligence—has been a hot topic as of late, with it seemingly being used for any purpose you can imagine nowadays. Unfortunately, this has also included cybercrime.
However, just as AI can be a weapon for cybercriminals to use, it can also be a shield to help protect your business from threats. For instance, in phishing prevention.
Every office has that one person that doesn’t seem to care that they are working in a room with other people. You know the type: They have day-old food on their desk. There are papers and other unnecessary items strewn about the desktop. Things are sticky and smell strange. The funny part is they seem comfortable with that mess. They may be the only one that is. In this week’s blog, we discuss the benefits of keeping your workspace clean.
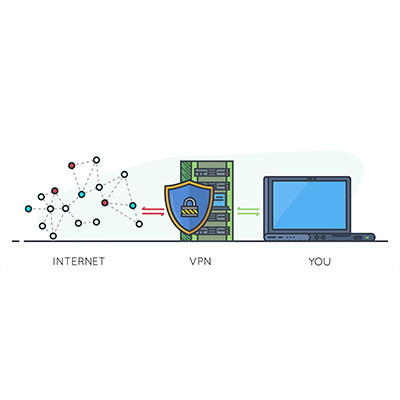
When it comes to security, one often overlooked tool is the virtual private network, or VPN. We recommend that all businesses use a VPN to keep remote and hybrid workers from inadvertently putting your business’ data at risk while out of the office. Let’s go over why a VPN is so effective, as well as what you should look for in a business-grade VPN tool.
Have you ever struggled with storage space on your Android device? For individuals who have, we bet that downloading applications that you ultimately don’t end up using very often is a major culprit here. To help you clear up storage space on your device, Android will receive an auto-archiving feature that can save you significant amounts of storage space by archiving your unused applications.
Your business depends on its bandwidth and its Internet connection to remain productive, part of which means ensuring that you have a reliable and stable wireless connection. How can you set up your network so that it is optimal and efficient? We have some thoughts on the matter and want to share them with you.
Businesses cannot afford to grow complacent with their network security, as it could make a significant difference between falling prey to an attack and remaining secure. The process of securing a network must be looked at holistically, from top to bottom. This idea of enterprise security is not new, but even a small business needs to keep it in mind, and these solutions are more accessible than you might think.
Sustainability is a hot topic nowadays, from how we conduct ourselves in our personal lives to how businesses go about their respective business. If this is something that you want to promote in your business, we figured that the day before Earth Day was as good a day as any to share some of the ways you can do so.
We’ve been spending the past few weeks examining productivity and how to optimize it, and today, we felt it was necessary to address the issues that could throw the proverbial wrench into the works.
Don’t worry, though, we’re also going to touch on how you can avoid and/or mitigate the issues that might threaten your productivity.
One of the reasons that information technology keeps changing is for the sake of the user and their convenience using it. However, if this convenience comes at the sacrifice of your business’ cybersecurity, it just isn’t worth it. This is the crux of why we always recommend that any organization seeking to use password management should invest in a reputable password management software, rather than the built-in capabilities of modern browsers.
If you frequently use your desktop to store icons and files, and if you’re like most people who do this, you probably have a cluttered desktop that is difficult to manage. While you can and should take time to clean it up from time to time, one quick way you can do so is by adjusting the size of the icons found on your desktop.
Productivity has been, is now, and likely will forever be heralded as one of the preeminent goals for any business. As such, it makes sense to understand as much as we can about it. To do so, we’ll be examining a different aspect of productivity for the next few weeks.
First up: what is productivity, in the first place?