As a business professional, it’s your responsibility to protect your company’s digital assets from cybercrime, but the path forward is not always so easy or clear-cut. Without a thorough knowledge and expertise of IT security at your disposal, it can be challenging to protect your infrastructure as adequately as it needs to be. Here are some of the common issues that involve cybersecurity, as well as how you can address them.
Apex Technology Blog
The past few years have made many people understandably antsy about their health and spending extended amounts of time around other people—which can make coming into the office a very, very stressful experience for some. How can you make your office a healthier place so your team can feel a little more secure as they work?
For a business, communications take several forms. You have the telephone, instant messaging, email, and other collaboration mediums. On top of that, most businesses have some way to communicate with customers outside of the main options. That’s a lot of communication tools to manage and keep working effectively. This month we thought we would talk a little bit about the benefits of unifying your communications platforms for added benefit.
Your business is your livelihood, so it only makes sense to invest in its protections so that your livelihood is secure. This will require a strategic approach. Let’s go over what your business needs to remain sufficiently secure, and what you should look for from each to get the best, most secure option.
What kind of productivity suite does your business use for its day-to-day operations? It doesn’t really matter which industry you classify yourself as or what size your company is; a productivity suite will undoubtedly transform the way your organization operates. Let’s take a look at some of the most common applications found in productivity suites and how they can be powerful catalysts to get work done faster and more efficiently.
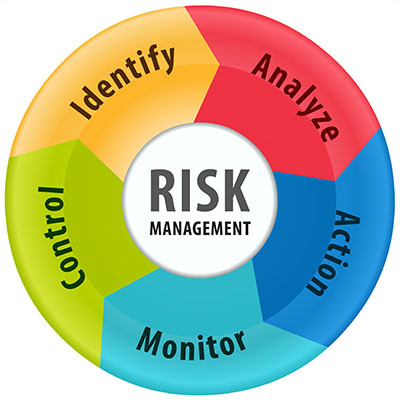
We’ve been known to take a bit of an extreme approach to cybersecurity—your business is at constant threat of being attacked by all manners of threats and all that. While we stand by this approach as an effective way to boost awareness and adherence to cybersecurity needs, there are certain attacks that are more likely to target you. This is where risk management comes into play.
Let’s get right to brass tacks. Your business is likely vulnerable to cybersecurity attacks. There are a whole lot of things you should be doing to protect your organization, but this one task is something you can do right now to save your business a lot of stress if something were to take down your network and cause a major disruption.
The server is the heart and brain of a business’ computing infrastructure. So much so that a failure can cause catastrophic effects on your business. If you are at a point where you are thinking about adding a server to your infrastructure, or replacing one that is a little long in the tooth, you now have less of a dilemma than you may have had previously. This doesn’t mean that it is not a serious decision, but today you have options on how you want to go about deploying your new server. This month, we thought we would go over some of the pros and cons that come with adding new infrastructure and whether purchasing a new server outright is the right decision for your business.
Have you ever wondered how some platforms will only have you log in once for all of your various needs, even though they might be different applications, websites, or services? This is essentially what single sign-on is, and it’s quite common in the technology world today. What is single sign-on exactly, and what kind of security does it actually provide for organizations that use it?
Sticky Keys—the Windows accessibility feature that keeps modifier keys like Shift and Ctrl active after you’ve pressed them—have a legitimate and necessary purpose for some. However, those who don’t need Sticky Keys can find them immensely annoying. Let’s go over how to deactivate sticky keys if you don’t need them.
Remember about a decade ago when all of the tech experts were predicting that most work would be done on a touch-screen device, prompting many professionals to purchase the latest and greatest tablets? Although tablet sales have not kept up over the years, they are still perfectly usable for personal purposes—maybe just not in the workplace. Still, we have to ask, is there a place for tablets in the office environment?
With cloud computing working wonders for small and medium-sized businesses of all types, you may gain confidence in finding hosted platforms that can help your business. Make no mistake about it, the cloud can work for your business in one way or another. This week, let’s go through how cloud options can help you improve your business’ computing.
When you virtualize a software solution, you are essentially storing it in an online environment where it can live. In other words, it remains in the cloud and is accessed through the Internet. This approach is helpful for many businesses, so why not flip this concept on its head and give hardware virtualization a shot? You might find that virtual workstations, for example, offer many benefits that can help your company be more productive and efficient.
The cloud is a great business tool and resource, enabling businesses to offset a lot of their IT workload onto these providers. If you haven’t migrated some or all of your business’ technology to take advantage of the cloud, it is certainly something to consider.
If you’re already considering it, we wanted to offer a few tips to help make the process more effective for you.
Have you ever wondered why it sometimes takes longer than you might expect for certain tasks to be accomplished with your business’ network? It turns out that technology is far from a simple thing, and small issues can seriously derail productivity and efficiency of complex information systems, one of which is the notorious network bottleneck. How can you identify and rectify this issue for your network?
How has your business managed its technology in recent years? Depending on the way you have done so, you could be unnecessarily throwing money down the drain when you could instead be reinvesting it into your organization. If you are ready to take your operations to the next level, consider changing your approach to your office’s technology management with managed services.
Every expense that your business takes on needs consideration. When you are looking to keep your business productive, you need to focus on keeping downtime to a minimum. In order to do that you need to have tools that don’t take a lot of work-time maintenance and have professional perspectives available that can help keep operations running when issues with your business’ technology do happen.
One of the primary ways that modern companies work to boost efficiency is to ease the workloads that their employees have to contend with through automation. Automating certain processes frees up the time these processes would otherwise take to devote to revenue generation. This approach has worked for decades—and today, businesses have access to more automation-focused technology than ever.