Data breaches—any event where a business’ confidential data is viewed, copied, or stolen by an unauthorized person or party—are a serious problem. Unfortunately, they are also a serious problem that can be caused by no shortage of situations. Let’s review some of the causes of business data breaches so you’ll know what to keep an eye out for.
Apex Technology Blog
Passwords have been a primary data security measure since 1960, when MIT researcher Fernando Corbató suggested the practice—although even he is reportedly slow to take full credit. Why? Well, if you ask Corbató (and his contemporaries, who were the first to implement passwords as we’d recognize them today), the security concerns were limited.
So, have we reached the point where it would be best to replace passwords as the default authentication measure?
We’ve all seen our friends and family sharing quizzes on their social media profiles, prompting people to find out what their celebrity stage name or what Hogwarts house you would be in, or to share what their first concert experience was. These fun, lighthearted quizzes are a great way to get to know a little more about the people we’re connected with… and that’s the biggest problem.
Gauging the effectiveness of your cybersecurity can be a bit of a daunting task, especially when asking if it could make a major difference in protecting your organization’s network infrastructure. If you want to track and measure your business’ cybersecurity preparedness, here are four steps to help you perform an evaluation.
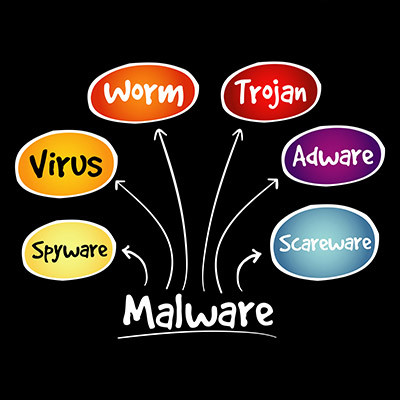
Network security could mean any number of things, but more often than not, people are using the term as a blanket statement against the dreaded idea of malware and its many forms. Today, we are discussing how vast the world of malware can be and how often you might find yourself misunderstanding what it exactly is. Knowing all this can help you identify if you have become a malware victim or not.
More workplaces than ever before are utilizing the power of remote technology, but this also creates problems with security that must be addressed. How can you ensure that your organization isn’t putting itself at risk as a result of this general displacement of your workforce? Let’s discuss some action items you might choose to implement for your business.
When we talk about data privacy in a business, the default is to generally think about the data the business has collected and compiled from its clientele. However, that’s just one type of data a business has. There’s also a lot of data that is collected by the business about that business’ employees. So, how well protected is this data?
Cybersecurity is an important subject for a business’ entire team to appreciate, particularly when it comes to the minute differences between different terms. For instance, a layperson might hear “breach” and automatically think “security incident.” While this technically isn’t incorrect, per se, the two terms aren’t really synonymous.
Let’s take a few moments to dive into the minutiae and define these two terms more clearly.
Ransomware is widely regarded as one of the worst modern cyberthreats out there today, and there's plenty of evidence to support this. These attacks and their aftereffects can devastate businesses of all industries. Let's consider why it is that ransomware is so dangerous, and what can be done to fight it.
There are times when you experience computer problems and you might hesitate to call in the big guns to resolve the issue. Unfortunately, the reality is that many businesses are under the impression that calling experts to handle their computer problems will leave them in a difficult position financially. We’re here to make sure that doesn’t happen! Here are three common computer repair problems that you might—just might—be able to solve in a simple and easy way.
If there is one shared priority most businesses and other organizations need to have it’s a strategy on how they are going to go about securing their network, infrastructure, and data from the numerous threats they face. Let’s take a look at three of the most crucial issues surrounding organizational cybersecurity as we head into the new year.
Smart devices and Internet-of-Things devices in general have taken the world by storm, and a home without at least a handful of smart devices is quite rare to find these days. However, smart devices—or devices that connect to the Internet to perform various functions—must be approached with a certain level of caution.
The holiday season has a variety of famous key players, including the likes of Santa, Rudolph, and the rest of the North Pole crew. Each year, they use their magic to help spread goodwill and joy to all the nice children of the world… but did you know that they are also responsible for protecting those who make the naughty list from Santa’s villainous counterpart, Krampus?
As the official managed service provider for Santa’s operation, we have been cleared to share the story about how we’ve helped defy Krampus to save Christmas.
Data breaches are an unfortunate reality in this day and age, even during the holiday season. While it is important to do everything you can to prevent these kinds of disasters, you need to be prepared to deal with it—both in terms of your operations, and in terms of communicating with your clientele.
There’s no way around it; ransomware is bad stuff, plain and simple. The first half of 2021 saw a massive increase in ransomware attacks that made the lives of countless individuals and business professionals difficult. However, a new trend is surfacing, and it’s one that you might be surprised to see: fake ransomware threats.
Twitch, Amazon’s popular streaming service where gamers and content creators broadcast to wide audiences, recently suffered a data breach. Thanks to this data breach, folks on the Internet now know just how much these content creators make, and it has exposed a whole new issue that Amazon must resolve.
Many threats immediately make themselves known on your device the second they install themselves, like ransomware and other types of malware. Others, like this newly discovered threat called MosaicLoader, discreetly install themselves in the background of your device and cause problems behind the scenes.
Data security isn’t a matter to be taken lightly, as too many businesses have found out the hard way. Unfortunately, there are far too many simple ways to correct common security issues - enough that it’s foolish not to do so. We’ll review a few ways to fix security issues, after discussing one of, if not the, most egregious security failings in modern history.